Trending Assets
Top investors this month
Trending Assets
Top investors this month
Snowflake Cybersecurity Workload $SNOW
As I am parsing the many product announcements coming out of Snowflake Summit, the new Cybersecurity Workload is worth calling out independently. It was first introduced a little over a week ago. This workload’s purpose is to help customer organizations detect and respond to threats by leveraging the Data Cloud for their security analytics. During Summit, the Snowflake team hosted a separate Cybersecurity track which included 15 sessions and presentations from a number of customers. This level of engagement likely explains why Snowflake pre-announced the availability of Cybersecurity workloads, versus bundling it with the other product announcements this week. As an aside, I am planning to publish coverage of the rest of Summit shortly.
First – does this announcement mean that Snowflake is now a security company? They aren’t in the conventional sense, but that’s what I think makes this product move so interesting. Every existing security analytics service is built on top of a large scale data processing platform. Some security analytics providers, like Splunk, Datadog and New Relic, built their own data processing engines from scratch 10 or more years ago. Elastic leverages the open source project Elasticsearch for security analytics, which they also maintain. Even the endpoint vendors have been adding data processing engines to supplement their XDR capabilities. Crowdstrike acquired Humio and integrated it into the Falcon platform. Sentinel One made a similar acquisition with Scalyr.
As Snowflake is already a high scale data platform for generalized analytics, they are moving into the security space in a different way. They are allowing customers to power their internal security monitoring practices using Snowflake as the data collection, processing and analysis platform. To supplement these efforts, Snowflake has lined up several third-party companies who will collect and process the data on the customer’s behalf, adding their own security analysis and threat detection. I think the Cybersecurity Workload offering would appeal to Snowflake customers on two levels.
First, some companies prefer to to build their own in-house security practices which leverage employee security experts for threat hunting. In this case, these teams want access to raw log data to craft their own queries and to code algorithms that identify threats. They can work with the DevOps team to get log data from server and network infrastructure sources loaded into their Snowflake instance. They can also combine this data with signals from other enterprise applications, like the HR or ITSM systems.
This approach was highlighted by a new customer for the Cybersecurity Workload, Figma. Figma is a SaaS-based collaborative product design tool. It allows teams to interactively mock-up user interfaces for web and mobile apps. Figma is using the Cybersecurity Workload to combine all the information sources available for security context, both internal and some third party data. This is work they might otherwise use Splunk or Elastic to perform.
Other customers may prefer to let third-party vendors power the security analysis layer. These Snowflake partners have built connected applications on top of the Snowflake Data Cloud. They connect to the end customer’s infrastructure devices (servers, network, databases other endpoints) to source log data. Then, they process the source data and store it in the customer’s Snowflake instance. This approach allows the third-party vendors to perform the security analytics, visualization, threat detection and response on the customer’s behalf, reducing their need to hire security experts. For cybersecurity analytics, Snowflake has lined up several partners, like Hunters, Panther Labs and Securonix, through their Powered By program.
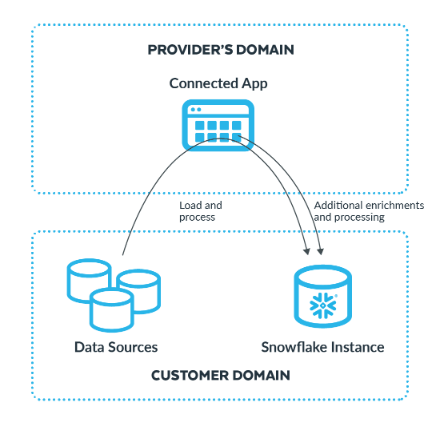
During Summit, two of Dropbox’s Senior Security Engineers discussed how they are making use of the Cybersecurity Workload, with partner Panther Labs providing the security analytics. In this case, Snowflake provides the data repository and underlying compute engine. For a company an expansive as Dropbox, Snowflake’s scale in data processing is needed to handle their large data volumes. Presumably, Snowflake realizes cost efficiencies on their data platform that other SIEM providers are challenged to achieve.
Snowflake announced a number of existing customers who are taking advantage of the new Cybersecurity Workload offering, including CSAA Insurance Group, DoorDash, Dropbox, Figma, Guild, Capital One and TripActions. These customers get the benefit of re-use of their data, some of which is already being collected and stored in Snowflake as part of their generalized analytics practice. By piping additional log data to their Snowflake instance and activating the Cybersecurity Workload, these customers can leverage the data they already have and keep it all in one location. This creates efficiencies and cost savings. It also prevents duplicating data collection and storage for security analytics, by using a stand-alone service with another vendor.

With the release of the Cybersecurity Workload, customers get the following benefits:
- Access to the power and elasticity of Snowflake’s platform to natively handle structured, semi-structured, and unstructured logs.
- Efficiently store years of high-volume data, search with scalable on-demand compute resources and gain insights using universal languages like SQL and Python.
- Organizations can unify their security data with enterprise data in a single source of truth, enabling contextual data from HR systems or IT asset inventories to inform detection and investigations.
- Unified visibility across their security posture, eliminating data silos without prohibitive data ingest or retention costs.
- Beyond threat detection and response, the Cybersecurity workload supports other use cases including security compliance, cloud security, identity and access, vulnerability management.
From a strategy and investment thesis perspective, I think there are several advantages to Snowflake’s approach. Fundamentally, it allows Snowflake to expand its reach into new types of data intensive workloads. However, it is doing that through a smart balance of leveraging their strengths in large scale data processing without having to make the investment in building an internal security threat hunting practice.
Some advantages include:
- Cost and scale. Because Snowflake already processes enormous volumes of data for their other analytics functions, they can likely perform security analytics at a lower cost than other cloud-based SIEM providers.
- Reduces copies of data. Stand-alone SIEMs are effectively collecting and maintaining a separate copy of a company’s data for security analytics. This poses overhead in maintaining data collection agents, network traffic, potential security risks and extra cost.
- Access to more signals. Threat hunters can combine infrastructure logs with data from other internal systems like HR or ITSM. Those may not be available to a separate SIEM.
- Let the experts be experts. By partnering with other companies for the security expertise, Snowflake focuses on their strengths in data processing.
- Access to third-party data in the Marketplace. Customers can subscribe to data feeds in the Snowflake Marketplace that can enhance their threat detection. Ingesting these feeds is simple through Snowflake data sharing.
- Revenue from Powered By partners. When Cybersecurity partners handle the security analytics, Snowflake still generates revenue from their use of storage and compute on the Data Cloud. During the Investor Session as part of Summit, Snowflake’s CFO revealed that 9% of their $1M+ customers are members of the Powered by program. This will continue to be large driver of revenue.
On the flip side, I don’t expect this to dislodge the pure play security companies, like Crowdstrike or Palo Alto Networks. Snowflake will likely capture spend from companies building their own internal security operations practice versus outsourcing everything to the full-service security companies. Also, the Cybersecurity Workload primarily targets existing or potential Snowflake customers. If the customer’s data is on BigQuery or another data cloud, the offering is less relevant.
It will be interesting to see how this product develops. I am encouraged by the initial traction with some highlighted customers. Personally, I can see the advantages of moving heavy security analytics workloads over to Snowflake simply to reduce cost and duplication of data. If the Powered By partners take off, they will generate significant consumption of Snowflake resources as well. I think that could become a large contributor to future revenue for Snowflake, as they get to place multiple bets on emerging players in security protection.
www.snowflake.com
Powered by Snowflake | Snowflake Data Cloud
With Powered by Snowflake, learn how to build, market, and operate applications in the Data Cloud. Build better faster and grow your business.
Already have an account?